PCI P2P Encryption with Bluefin
Services:
nAuthorization
nStand-alone credit
Processors:
This feature is supported for all processors that are supported for card-present transactions. See Supported Processors.Device:
nID TECH SREDKey PCI Key Pad with Encrypted MagStripe Reader
|
|
You must use a device that meets the following requirements: nIs provided by Bluefin Payment Systems unless otherwise agreed to by Cybersource and Bluefin nIs injected with encryption keys for the Cybersource payment card industry (PCI) point-to-point encryption (P2PE) solution, which is powered by Bluefin You need to have separate devices for sandbox testing and production. |
You must have a contractual relationship with Bluefin Payment Systems for PCI-validated P2PE services, which include:
nKey injection
nDecryption, which is performed by Cybersource
nHardware
You must manage your Bluefin devices through the Bluefin P2PE Manager portal, which enables you to:
nTrack device shipments
nDeploy or terminate devices
nManage users and administrators
nView P2PE transactions
nDownload and export reports for PCI compliance
Do not use terminal configuration #3 or #5, which causes the device to prompt you for the cardholder’s street address. To include the cardholder’s street address in your order management system, include the API field for the billing street address in your request.
The PCI P2PE solution, which is powered by Bluefin, does the following:
nSafeguards card data at the terminal hardware level
nReduces your PCI burden by minimizing the number of PCI audit questions to which you must respond
nProvides device life cycle management through the Bluefin P2PE Manager portal
nSupports magnetic stripe read (MSR) and manual key entry
The following diagram illustrates the steps in a transaction that uses encryption:
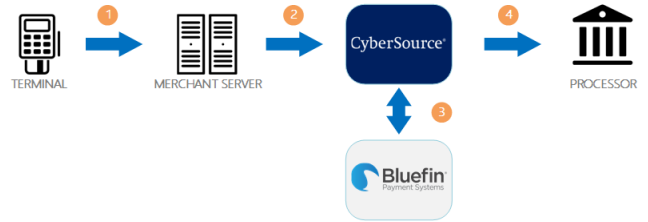
1When a customer swipes a card through the Bluefin device, the device encrypts the card details at the hardware level and in accordance with PCI P2PE standards. The device sends the encrypted payload to your order management system.
2Your order management system sends the encrypted payload to Cybersource in an authorization request or stand-alone credit request.
3Cybersource sends the encrypted payload to Bluefin to be decrypted and parsed. Bluefin sends the decrypted data to Cybersource over a secure channel.
4Cybersource sends the decrypted data and additional transaction information to your processor.
Creating a Request for an Authorization or Stand-Alone Credit That Uses Bluefin PCI P2PE
|
|
When using the Simple Order API in XML format, you must use version 1.132 or later of the XML schema to use Bluefin P2PE encryption. |
For examples that use Bluefin PCI P2PE, see:
nName-value pair examples: Authorization Using Bluefin PCI P2PE
nXML examples: Authorization Using Bluefin PCI P2PE
Step 1Include the following fields in the request:
nencryptedPayment_data
nencryptedPayment_descriptor
These fields are described in P2PE Request Fields.
Step 2Include general card-present request fields in the request as needed. See General Card-Present Request Fields.
Step 3Follow instructions in Credit Card Services Using the Simple Order API for creating an authorization request or stand-alone credit request.
|
|
Most of the fields that are normally required for an authorization request or stand-alone credit request are not required for a Bluefin PCI P2PE request because the encrypted data includes most of the required data. |